WWW Homepage Access Counter and Clock!
Three-in-one (Counter+Clock+Date)
[Count Release 2.2]
Latest Release: January 16, 1996
Initial Release: April 13, 1995
----------------------------------------------------------------------------
[Image] [Image]
If you see the counter, clock or date image as 888888, then you
are using a browser which can not be trusted. For untrusted
browsers, no counter hit is recorded, no time or date is displayed
and the literal digit string is displayed. This feature guarantees
that the counter can not be accessed remotely to mess up the
datafile from a browser like yours. I consider a browser untrusted
if it does not return the environment variable HTTP_REFERER. Some
entries in the log file are made including the browser type.
Note, this strict mode of the program is experimental at this
time. You can decide whether you want this option or not while you
run the Count-config script.
-------------------------------
Counter announce list
If you want to receive announcement of future release of the counter,
send mail to:
muquit@semcor.com
In the Subject line, write (in lower case):
subscribe counter
If anyone want to maintain a mailing list, go for it!
Table of Contents
* Requirements
* Introduction
* Features
* Digit styles
* Obtaining source archive
* Directory Structure
* Steps to compile and install
* Test the program from command line
* How to call the program from web page?
* Examples
* What is "Counter Terrorism"? And how this program handles it?
* Error messages
* Frequently asked questions
* Copyright
* Acknowledgment
* Authors
* Please Add your URL!
* Web pages using the counter
* I like to hear from you
* ChangeLog (if you contributed, your name is there)
Requirements
* Unix Operating System.
This version (2.2) is not ported to any OS yet. For NT and OS2 port,
please visit the web page for Count 1.5.
* A C compiler (ANSI or non-ANSI).
* You must have root access and basic concept of Unix system
administration (to install). If your site is configured to run CGI
program from users' space, then you will not need root access.
* You must run a httpd daemon (tested with NCSA,CERN and APACHE httpd).
It also works with Netscape Communications Server (reported by Scott
Barnhill (cosbarnh@ihc.com). However it should work with any unix http
server which supports CGI programs. I personally run APACHE httpd 1.0.
I think it's the best freely available http server for Unix.
This program is compiled and tested on a Sparc 10 (SunOS 4.1.4) running
NCSA httpd 1.4 , CERN httpd 3.0, APACHE httpd 1.0, (gcc 2.6.3).
Count 1.5 runs on:
[Linux] | [Solaris 2.x] | [BSDI] | [SGI IRIX 5.3]
[AIX 3.2.5] | [HP-UX-?] | [Ultrix 4.3] | [SCO]
[AT&T Unix SVR4] | [DEC Alpha 3000/300L with OSF/1]
This version should be portable as well.
Introduction
This is a CGI program to keep record of the raw hits of a web page. It
generates a GIF image of the number of hits and returns to the browser
as an in-lined image. The program also has run-time option not to show
the digit images, this way the hits can be kept without displaying it.
The hits can be be monitored without incrementing from a separate page
as well. Almost all of the features are run-time options. The hits are
no way accurate. Someone can reload the page again and again to
increase the hits. However, people like to see how many times someone
visited their page. The same program can be used to count hits for any
number of web pages for any number of users. The program can be used to
display time or date as well. The time or date of any place in the word
can be displayed by specifying a timezone string for that location. The
date can be formatted in any combination of MMDDYY (Month-Day-Year).
This program started as a fun to play with CGI programming but due to
enormous interest, and feature request, it has turned in to the most
configurable counter on the web.
The program is distributed as a gzip'd tar archive. If you do not have
gzip/gunzip, it's available at: prep.ai.mit.edu.
Features
+ Does not require server-side includes.
+ Count 2.0 is backward compatible with Count1.5's URL. One thing to
note, the keyword wxh has no meaning in Count 2.0. It was used in Count
1.5 to specify digit dimensions. In Count 2.0 it is not required,
because the digit dimensions are determined automatically. Therefore,
you can use variable width digit images in this version.
+ Reasonable default for all QUERY_DTRING parameters.
+ The same program can be used to display time or date.
+ The time and date of any place in the world can be displayed.
+ Supports digit images with variable width.
+ Counter can be displayed without incrementing (for monitoring etc.)
+ A literal digit string can be displayed.
+ A random digit string can be displayed.
+ The color of the digits can be negated.
+ The counter can be rotated (only integral of 90 degrees, 90,180,270).
The default rotation is 270 degrees.
+ An ornamental 3D frame can be wrapped around the counter image with
user defined thickness and color at run time.
+ The frame and transparent color can be a name (e.g. red,green,pink
etc.). The color can be specified as a hex string, e.g. ffffff, ff0000
etc. as well as RGB triplets as before.
+ Single program for any number of users for any number of web pages.
+ Any color of the counter image can be made transparent at run time.
+ Style of digits can be specified at run time.
+ Authorized host names can be in the configuration file. To handle
"Counter Terrorism", (looks like this page is dead!) the source code
modification is not necessary.
+ IP filtering through a configuration file at run time. Any number of
hosts can be ignored from counting. Wildcard can be used for IP address
in the configuration file to ignore hosts from counting. For example,
to ignore host in a Class C network, host name can be 192.160.166.*,
for Class B network, 128.66.*.*, for Class A network, 26.*.*.*.
Therefore all hosts in a domain can be filtered out this way. It's a
good idea to ignore your own host or entire domain. Gen-conf program
will let you create the configuration fiel interactively.
+ Advisory data file locking. Data file will not get messed up by
simultaneous Count.cgi processes. Advisory data file locking is
superior to ancillary file locking because advisory locking is handled
directly by the Operating System.
+ Maximum number of digits can be set or counter can be displayed with
exact number of digits at run time.
+ User will be able to specify a start-up counter value at run time. This
will take effect if the data file does not exist. You will be problem
by the configuration program if you want this feature or not.
+ If you do not want to display the counter but like to keep the hits on
your page, sh=0 can be defined in the QUERY_STRING at run time. It will
write a 1x1 transparent GIF image to the browser but the counter in the
data file will be incremented all right.
Obtaing source archive
The source code for this program is distributed via the Web as a gzip
compressed tar archive. If you do not have gzip/gunzip, it's available
at: prep.ai.mit.edu.
This machine is getting enormous number of ftp requests lately.
Therefore, I had to impose a limit of maximum 10 ftp connections at one
time. The limit will go up to 50 maximum connections at 11:00 PM US
Easern Statndard Time and go back to 10 maximum connections at 6:00 AM
US Eastern Standard Time.
Sorry for the inconvenience!
[ftp] Download source archive
The file wwwcount2.2.tar.gz is a gzip'ed tar file. To extract the
distribution, at the shell prompt, type:
gunzip < wwwcount2.2.tar.gz | tar xvf -
cd wwwcount2.2
The program will compile with ANSI or non-ANSI C compiler.
Directory Structure
Before going to the configuration procedure, please browse through the
default directory structure below. It will help you answering questions
of the configuration script. You can change the name of the directories
as you please, but keep the directory structure same, it will make your
life much easier. You do not have to create any of these directories,
they will be created for you by the Count-install program. Only thing
you probably have to create are the individual datafiles (keep
reading).
[image]
Base Directory is the directory where all the sub-drectories and the
files releated to counter reside.
Log Directory is the directory which holds the counter Log file.
Counter error messages or if someone tries to acces your counter
remotely, warning message regarding this is written to this file.
conf directory holds the configuraion file for the counter. The
configuration file holds information in 2 blocks. Each block resides
between a left and right curly brace. The first block is called "ignore
hosts" block. "ignore hosts" block defines the IP addresses of the
hosts to ignore from counting. For example, if a user is running the
web browser at the host 192.160.166.100 and if 192.160.166.10 is
present at this block, the counter will be displayed but not
incremented. You might want to put your own IP address here. The second
block is authentication block. This block contains the hostnames, IP
addresses, aliases for the hosts if any. All hosts present on this
block will be able to access the counter locally or remotely, if others
try to access, they will be denied. This file is created by the program
Gen-conf and can be hand crafted later.
data directory holds all the datafiles for the counter. The datafiles
stores the access counts of web pages. Each page must have a separate
datafile. The datafile is specified at run-time. You will know about it
later.
digits directory holds sub-drectories with various styles of GIF
digits. For example, A sub-directory holds the green led digits. The
sub-directories have GIF digit files named zero.gif,
one.gif...nine.gif. you will know about it later.
rgb.txt file is used to convert a color name (for example, cyan) to the
appropriate red, green and blue color component. This file came from X
consortium and supplied with the distribution. You will know about the
file later.
Digit Styles
The digits used in this program are individual GIF files. This gives
flexibility of using digits of your choice. The digit images are named
as zero.gif, one.gif,.... nine.gif. At run-time, simply the directory
of the images is specified to use a different style. Therefore, a
single program can generate digits of various styles. Here are the
supplied digit styles.
Style A [styleA] designed by me (digits/A)
can be used for clock or date.
Style B [styleB] Borrowed from HTML-access counter. (digits/B)
Style C [styleC] designed by benjamin@pop3.oro.net (digits/C)
Style D [styleD] designed by me (digits/D)
can be used for clock or date.
Style E [styleE] designed by me (digits/E)
can be used for clock or date.
A suggested use of style E is to make the white color transparent (you
will know about transparency later).
For a huge collection of GIF digits, check out the Digit Mania page.
This program will work with any digits from the Digit Mania page. To
use those digits, create subdirectories say, F,G, H etc. inside the
digits directory and rename the images to zero.gif, one.gif..nine.gif.
To use those digits for clock or time, make sure you have or create
am.gif, pm.gif, colon.gif and dash.gif.
Steps to compile and install
In the current release of the counter, there should not be any need for
hand editing any files. Several configuration scripts are supplied to
automate the whole process. I am giving a little description about the
scripts just may be you are curious:
Count-config
script to generate the header file config.h, a variable template file
for install program.
configrue
script to generate correct Makefiles for any Unix system.
Gen-conf
script to generate the configuration file.
Count-install
script to install the Count binary Count.cgi, digit images,
configuration file and the rgb color name database to the correct
places.
Now at the shell prompt (shell prompt is where you type ls, read your
mails etc.), type the following commands in the described order and
press Return key:
./Count-config
The script will ask questions with brief description. Answer them.
Look at the directory structure image to better understand the
questions.
Look at a sample session
./configure
The script will not ask any questions, but you will see the
informational messages about your system. It will create the
Makefiles (Makefile and combine/Makefile) for your system.
Look at a sample session
make clean (not needed if you compiling the first time)
make
Compilation will start if the previous two scripts completed
successfully. It will take some time. If compilation succeeds, go
to the next step.
./Gen-conf
This script will ask you questions about your system. Answer them.
This process will create the configuraion file for the counter.
Look at a sample session
./Count-install
This is the final step. This scripts will install the necessary
things for the counter in your system. You will need root access
if you are installing it an area where root access is needed. This
program will ask you couple of questions.
If you finished all the above steps successfully, you are ready to test
the counter. Go to the next section.
Test the program from command line
A shell script is supplied for testing the counter. the name of this
script is testcount-sh. Look at this script, you might need to change
certain things. Please read the comments in this script for
understanding the various run-time options of the counter. You'll also
know in detail about the options in the section How to call the
program.When you are happy with everything, save it and at the shell
prompt type:
./testcount-sh
How to call the program?
You can refer to the program from web page like this:
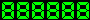 The string between ? and " is called the QUERY_STRING. Make sure there
is no newlines in the
The string between ? and " is called the QUERY_STRING. Make sure there
is no newlines in the  count.dat
The counter program has lots of options, you can make it work and look
the way you desire. In the query string, you can use the options
described in the table below. The options can be separated by a | or a
&. You can use either one or both. Here is an example:
count.dat
The counter program has lots of options, you can make it work and look
the way you desire. In the query string, you can use the options
described in the table below. The options can be separated by a | or a
&. You can use either one or both. Here is an example:
 The options can be in any order and not case sensitive.
Anyway, look at this Example Page you will get the picture.
Counter Options
[I stole it from Kevin's page :) ]
Parameter Name Description Default
A valid string can be
specified with display=
parameter to display
counter, clock or date.
The valid value for the
string parameter X is
counter,clock or date For
Specifies counter, this parameter is
display=X what to not need as counter is the display=counter
display. default display type.
Note: clock and date will
only work with digit style
A, D and E. If you want to
use a different style of
digits, you have to design
the dash.gif, am.gif,
pm.gif and colon.gif.
The parameter timezone= is
only significant with
display=clock or
display=date. Use this
parameter if you want to
display time or date of
another timezone. For
example, for eastern time
with daylight saving time,
timezone=EST5EDT, central
time with daylight saving
time, timezone=CST6CDT,
mountain time with
daylight saving time,
timezone=MST7MDT, pacific
time with daylight saving
timezone=X Specifies time, timezone=PST8PDT. None.
timezone.
for GMT, timezone=GMT. An
offset from GMT can be
used as well,
timezone=GMT+6. Note, the
GMT offset method may not
work properly with SYSV
type OS. Look at the
manpage for ctime,
localtime for your
machine.
If the clock displays your
local time wrong, you must
specify your timezone with
that parameter in order to
display the correct time.
This parameter is only
significant with
display=date. The valid
value for the string
dformat=X Specifies parameter X is any dformat=MMDDYY
date format.
combination of MMDDYY
(Month-Day-Year). For
example, dformat=ddmmyy,
dformat=YYMMDD.
You can wrap the counter
in an ornamental frame of
ft=X Frame X pixels thick. Use 0 for ft=6
Thickness
no frame. Values over 5
make a nice 3-D effect.
Specifies the color of the
frame in RGB
(red/green/blue) format.
Each color component, R,
G, and B is specified as a
value between 0 and 255.
If you use ft= without a
frgb= param, the default
color is used.
If you specify a frgb=
frgb=100;139;216
frgb=R;G;B Frame Color without a ft=, then the or
frame thickness defaults
to 5. All the examples frgb=648bd8
show ft=5. The color can
be specified as hex string
or a name. Do not use a #
before the hex string as
Netscape. For example, if
you want to specify white
in hex, you do
frgb=ffffff. Look at the
color name mapping
database for some hints.
You can specify if your
counter image will have a
transparent color with the
Boolean B. So tr=Y means
there will be a
transparent color; and
tr=N means there will not.
It does not matter if the
tr=B Transparency GIF files used for the tr=N
On/Off No Transparency
digits are "transparent";
you must specify
explicitly which color to
make transparent. If you
specify a trgb=, then you
do not need to specify
tr=Y. Valid values for B
are Y, N, T, F, 1, or 0.
Defines maximum number of
digits to display. Any
value between 5 and 10
md=X Max Digits inclusive are permitted. md=6
Padding with leading zeros Without padding
is automatically done for
you; longer counts are
truncated to the given X.
pad=N
Without
Turn padding on/off in specification of
conjunction with md= a md=value
pad=B Padding with setting. Valid values for
0's
the Boolean parameter B pad=Y
are Y, N, T, F, 1, or 0. With
specification of
a md=value
Denotes directory of a
specific styles of digits.
Four styles of digits are
dd=A
dd=A Digit suppiled. They are kept at My green led
Directory the directories A,B,C and
D respectively. Visit the digits
digit mania page for other
styles of digits.
Used to set the initial
value of the counter to
some number X. This is
only valid if you decided
to allow automatic
datafile creation. This is
a bad practice to compile
with this option, however st=1
st=X Start Count it makes site maintaining Count starts at
easier. Note that this 1
parameter has no effect if
the datafile alreay exist.
If you want to change the
counter value in a
existing datafile, hand
edit the file. The minimum
value for st is 1.
Used to turn display of
digits on or off according
to the Boolean B. When
sh=T, counter will be
displayed and incremented,
this is the default
behavior.
sh=B Show digits sh=Y
If sh=F no digits will
show, but the counter will
still increment; instead
of digits a transparent
1x1 GIF is displayed.
Valid values for the
Boolean parameter B are Y,
N, T, F, 1, or 0
Specifies the name of the
file for storing the count
in. The file must be
allocated to you as was
mentioned in the
"Authorizations" section
above. You can use
df=random to diaplay a
random number.
One special use of the
df=random
df=data_file Datafile to parameter is df=RANDOM. if no datafile
store count This returns a random
number using the is specified
fractional portion of the
host's time of day clock
as a seed for the
generator. Unlike all
other WWWcounter
parameters, the file name
provided is
case-sensitive, except for
the value random. Or
Random, or rANDOM, etc.
Makes it possible to
display the current count
without incrementing the
count. This can be used to
examine the count for incr=T
incr=B Increment reporting or other Increment the
Count counter on each
purposes without adding to
the count. Valid values invocation
for the Boolean parameter
B are Y, N, T, F, 1, or 0.
Makes it possible to
display a given,
lit=X Display predetermined value. Valid None
literal
values for the string X
are digits.
Makes it possible to
negate the color of the
counter digits. Note that
negate=B Negate the the Frame is exempted from negate=F
color Do not negate
negating. Valid values for
the Boolean parameter B
are Y, N, T, F, 1, or 0.
Makes it possible to
rotate the counter image X degrees=270
degree. The possible With rotate=Y
and without
degrees=X Rotate X values of X is 90, 180, degrees=X
degrees 270 and 360. Note 360 is
meaningless as the counter rotate 270
will come back to the degreess
original 0 degree. clockwise
The Boolean value B turns
on or off rotating. If you
use degrees= settting,
rotate=B Rotate rotate is not needed. rotate=F
On/Off Do not rotate
Valid values for the
Boolean parameter B are Y,
N, T, F, 1, or 0.
What is "Counter Terrorism"? And how this program handles it?
If you do not know, in most cases any CGI program can be referred
remotely. For example, a CGI program x.cgi (say it returns an in-lined
image) in foo.com can be called from foobar.com as follows:
The options can be in any order and not case sensitive.
Anyway, look at this Example Page you will get the picture.
Counter Options
[I stole it from Kevin's page :) ]
Parameter Name Description Default
A valid string can be
specified with display=
parameter to display
counter, clock or date.
The valid value for the
string parameter X is
counter,clock or date For
Specifies counter, this parameter is
display=X what to not need as counter is the display=counter
display. default display type.
Note: clock and date will
only work with digit style
A, D and E. If you want to
use a different style of
digits, you have to design
the dash.gif, am.gif,
pm.gif and colon.gif.
The parameter timezone= is
only significant with
display=clock or
display=date. Use this
parameter if you want to
display time or date of
another timezone. For
example, for eastern time
with daylight saving time,
timezone=EST5EDT, central
time with daylight saving
time, timezone=CST6CDT,
mountain time with
daylight saving time,
timezone=MST7MDT, pacific
time with daylight saving
timezone=X Specifies time, timezone=PST8PDT. None.
timezone.
for GMT, timezone=GMT. An
offset from GMT can be
used as well,
timezone=GMT+6. Note, the
GMT offset method may not
work properly with SYSV
type OS. Look at the
manpage for ctime,
localtime for your
machine.
If the clock displays your
local time wrong, you must
specify your timezone with
that parameter in order to
display the correct time.
This parameter is only
significant with
display=date. The valid
value for the string
dformat=X Specifies parameter X is any dformat=MMDDYY
date format.
combination of MMDDYY
(Month-Day-Year). For
example, dformat=ddmmyy,
dformat=YYMMDD.
You can wrap the counter
in an ornamental frame of
ft=X Frame X pixels thick. Use 0 for ft=6
Thickness
no frame. Values over 5
make a nice 3-D effect.
Specifies the color of the
frame in RGB
(red/green/blue) format.
Each color component, R,
G, and B is specified as a
value between 0 and 255.
If you use ft= without a
frgb= param, the default
color is used.
If you specify a frgb=
frgb=100;139;216
frgb=R;G;B Frame Color without a ft=, then the or
frame thickness defaults
to 5. All the examples frgb=648bd8
show ft=5. The color can
be specified as hex string
or a name. Do not use a #
before the hex string as
Netscape. For example, if
you want to specify white
in hex, you do
frgb=ffffff. Look at the
color name mapping
database for some hints.
You can specify if your
counter image will have a
transparent color with the
Boolean B. So tr=Y means
there will be a
transparent color; and
tr=N means there will not.
It does not matter if the
tr=B Transparency GIF files used for the tr=N
On/Off No Transparency
digits are "transparent";
you must specify
explicitly which color to
make transparent. If you
specify a trgb=, then you
do not need to specify
tr=Y. Valid values for B
are Y, N, T, F, 1, or 0.
Defines maximum number of
digits to display. Any
value between 5 and 10
md=X Max Digits inclusive are permitted. md=6
Padding with leading zeros Without padding
is automatically done for
you; longer counts are
truncated to the given X.
pad=N
Without
Turn padding on/off in specification of
conjunction with md= a md=value
pad=B Padding with setting. Valid values for
0's
the Boolean parameter B pad=Y
are Y, N, T, F, 1, or 0. With
specification of
a md=value
Denotes directory of a
specific styles of digits.
Four styles of digits are
dd=A
dd=A Digit suppiled. They are kept at My green led
Directory the directories A,B,C and
D respectively. Visit the digits
digit mania page for other
styles of digits.
Used to set the initial
value of the counter to
some number X. This is
only valid if you decided
to allow automatic
datafile creation. This is
a bad practice to compile
with this option, however st=1
st=X Start Count it makes site maintaining Count starts at
easier. Note that this 1
parameter has no effect if
the datafile alreay exist.
If you want to change the
counter value in a
existing datafile, hand
edit the file. The minimum
value for st is 1.
Used to turn display of
digits on or off according
to the Boolean B. When
sh=T, counter will be
displayed and incremented,
this is the default
behavior.
sh=B Show digits sh=Y
If sh=F no digits will
show, but the counter will
still increment; instead
of digits a transparent
1x1 GIF is displayed.
Valid values for the
Boolean parameter B are Y,
N, T, F, 1, or 0
Specifies the name of the
file for storing the count
in. The file must be
allocated to you as was
mentioned in the
"Authorizations" section
above. You can use
df=random to diaplay a
random number.
One special use of the
df=random
df=data_file Datafile to parameter is df=RANDOM. if no datafile
store count This returns a random
number using the is specified
fractional portion of the
host's time of day clock
as a seed for the
generator. Unlike all
other WWWcounter
parameters, the file name
provided is
case-sensitive, except for
the value random. Or
Random, or rANDOM, etc.
Makes it possible to
display the current count
without incrementing the
count. This can be used to
examine the count for incr=T
incr=B Increment reporting or other Increment the
Count counter on each
purposes without adding to
the count. Valid values invocation
for the Boolean parameter
B are Y, N, T, F, 1, or 0.
Makes it possible to
display a given,
lit=X Display predetermined value. Valid None
literal
values for the string X
are digits.
Makes it possible to
negate the color of the
counter digits. Note that
negate=B Negate the the Frame is exempted from negate=F
color Do not negate
negating. Valid values for
the Boolean parameter B
are Y, N, T, F, 1, or 0.
Makes it possible to
rotate the counter image X degrees=270
degree. The possible With rotate=Y
and without
degrees=X Rotate X values of X is 90, 180, degrees=X
degrees 270 and 360. Note 360 is
meaningless as the counter rotate 270
will come back to the degreess
original 0 degree. clockwise
The Boolean value B turns
on or off rotating. If you
use degrees= settting,
rotate=B Rotate rotate is not needed. rotate=F
On/Off Do not rotate
Valid values for the
Boolean parameter B are Y,
N, T, F, 1, or 0.
What is "Counter Terrorism"? And how this program handles it?
If you do not know, in most cases any CGI program can be referred
remotely. For example, a CGI program x.cgi (say it returns an in-lined
image) in foo.com can be called from foobar.com as follows:
 That is, someone somewhere on the Internet can refer to your counter
and increase the hits and you will not have a clue. You will get the
false impression of many people visiting your page. You can look at the
so called "Counter Terrorist" (looks like this page is dead!) page for
demo.
So how this program handles this? The counter program tries to get a
environment variable called HTTP_REFERER for remote referer. It is
necessary to check this variable because when someone remotely refer to
a CGI program to your machine, the variable REMOTE_ADDR will be the
address of your machine. So checking REMOTE_ADDR will not work. Most of
the moderm browsers returns the env variable HTTP_REFERER. If the
browser does not return the variable, counter will be served anyway.
But you are not lost totally here. If you decided to ignore count for
your host running httpd, the counter will be served but it will not be
increased. So, I suggest ignore count for your own host. Gen-conf
program is used for generating the configuration file. The second block
is the authentication block, that is hostname in this block will be
able to access the counter remotely as mentioned about.
Note this is a simple solution of a complex problem. It is not full
proof. Your feedback is always welcome in this regard.
Error Messages
Count will try to return an image in any event. That is, even if it
fails for some reason, it will write the error messages in GIF format.
The text error messages also will be written to the counter log file
defined with LogFile in the directory defined with LogDir in the
config.h file. The program Count-conf asked about these if you
remember.
If you see any of these images, please check the Counter log file you
defined with LogDir and LogFile. If the program could not create the
log file, it will write the error messages to stderr. In that case if
you configured your httpd server to write the log to a file, the error
messages will the written to this file.
Frequently Asked Questions
1. My CGI scripts don't work. What's wrong?
Copyright
Copyright 1995 by Muhammad A Muquit. Permission to use, copy, modify
and sell this program for any purpose is hereby granted without fee,
provided that this copyright notice appear in all copies and that both
that copyright notice and this permission notice appear in supporting
documentation, and the author's name not be used in advertising or
publicity pertaining to distribution of the software without specific
written prior permision. If the program is included in a book,
publication or software distribution media for sale, the author must be
notified about it.
THIS PROGRAM IS PROVIDED "AS IS" WITHOUT EXPRESS OR IMPLIED WARRANTY.
THE AUTHOR DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL THE AUTHOR Muhammad A. Muquit BE LIABLE FOR ANY SPECIAL,
INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING
FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT,
NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION
WITH THE USE OR PERFORMANCE OF THIS SOFTWARE. .
Note: This program is developed in my own time. My employer SEMCOR,
Inc. has nothing to do with it.
Acknowledgment
Thanks to John Cristy for ImageMagick. I took many routines from
ImageMagick for the GIF image combining library. I borrowed the font
array and some code from gd library. Thanks to Tom Boutell. Thanks to
Kevin J. Walsh. Without Kevin this release would not happen. Thanks to
all of you who showed interest in the counter program. I had fun
writing it.
Authors
Muhammad A Muquit and
Kevin J. Walsh
I like to hear from you
If you are using this program, I like to hear from you. Please add your
web page URL to the database via this form. You can drop me a line if
you like. If you are having any problem with the program, please let me
know as well. Feel free to send any suggestion. If you think that the
program is cool, please consider sending me a picture postcard of the
area where you live. Thanks to all of you who sent me the nice
postcards. I really appreciate it.
I receive enormous number of mails. Please understand that no way I can
answer all of the mails I receive, although eventually I read all the
mails. If you do not hear from me in 3 days, please resend the mail
again.
Muhammad A Muquit
SEMCOR, Inc.
65 West Street Road
Warminster, PA 18974
USA
Thanks.
Enjoy!
ChangeLog
If you contributed or suggested something and if your name is not here,
please drop me a line and get the credit.
Count 2.2 (January 16, 1996)
o There was a logic problem in determining AM and PM. Thanks to
(stephen@txdirect.net). 01/18/96
o Strict mode (detect if browser returns HTTP_REFERER) is a
configurable option.
o An error was in the code related to ACCESS_AUTH directive.
Reported by c2dhanle@CompApp.DCU.IE
Count 2.1 (January 15, 1996)
* The bug related to st parameter is fixed.
* The same program an be used to display time or date.
Count 2.0 (December 27, 1995)
* Configuration scripts. You should not to need to hand edit any
file in order to compile and install the counter.
* Reasonable defaults for all QUERY_STRING parameters.
Implemented by Kevin J. Walsh
* QUERY_STRING parameters can be in any order and not case
sensitive.
Implemented by Kevin J. Walsh
* Counter can be displayed without incrementing.
Implemented by Kevin J. Walsh
* A literal digit string can be displayed.
Implemented by Kevin J. Walsh
* A random digit string can be displayed as counter.
Implemented by Kevin J. Walsh
* Colors can be negated, that is counter can be displayed as a
negative copy.
* The counter can be rotated (integral of 90 degrees, 90,180,270
degrees).
* No need to specify width and height of digit images.
* The frame and transparent color can be a name (e.g. red, violet
etc), a hex string (e.g. ffffff, ff00ff, dddddd etc.) as well as
RGB triplets (e.g. 160;255;0, 0;0;0 etc) as before.
Implemented by Kevin J. Walsh
* The counter can be called as simply as:
That is, someone somewhere on the Internet can refer to your counter
and increase the hits and you will not have a clue. You will get the
false impression of many people visiting your page. You can look at the
so called "Counter Terrorist" (looks like this page is dead!) page for
demo.
So how this program handles this? The counter program tries to get a
environment variable called HTTP_REFERER for remote referer. It is
necessary to check this variable because when someone remotely refer to
a CGI program to your machine, the variable REMOTE_ADDR will be the
address of your machine. So checking REMOTE_ADDR will not work. Most of
the moderm browsers returns the env variable HTTP_REFERER. If the
browser does not return the variable, counter will be served anyway.
But you are not lost totally here. If you decided to ignore count for
your host running httpd, the counter will be served but it will not be
increased. So, I suggest ignore count for your own host. Gen-conf
program is used for generating the configuration file. The second block
is the authentication block, that is hostname in this block will be
able to access the counter remotely as mentioned about.
Note this is a simple solution of a complex problem. It is not full
proof. Your feedback is always welcome in this regard.
Error Messages
Count will try to return an image in any event. That is, even if it
fails for some reason, it will write the error messages in GIF format.
The text error messages also will be written to the counter log file
defined with LogFile in the directory defined with LogDir in the
config.h file. The program Count-conf asked about these if you
remember.
If you see any of these images, please check the Counter log file you
defined with LogDir and LogFile. If the program could not create the
log file, it will write the error messages to stderr. In that case if
you configured your httpd server to write the log to a file, the error
messages will the written to this file.
Frequently Asked Questions
1. My CGI scripts don't work. What's wrong?
Copyright
Copyright 1995 by Muhammad A Muquit. Permission to use, copy, modify
and sell this program for any purpose is hereby granted without fee,
provided that this copyright notice appear in all copies and that both
that copyright notice and this permission notice appear in supporting
documentation, and the author's name not be used in advertising or
publicity pertaining to distribution of the software without specific
written prior permision. If the program is included in a book,
publication or software distribution media for sale, the author must be
notified about it.
THIS PROGRAM IS PROVIDED "AS IS" WITHOUT EXPRESS OR IMPLIED WARRANTY.
THE AUTHOR DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL THE AUTHOR Muhammad A. Muquit BE LIABLE FOR ANY SPECIAL,
INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING
FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT,
NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION
WITH THE USE OR PERFORMANCE OF THIS SOFTWARE. .
Note: This program is developed in my own time. My employer SEMCOR,
Inc. has nothing to do with it.
Acknowledgment
Thanks to John Cristy for ImageMagick. I took many routines from
ImageMagick for the GIF image combining library. I borrowed the font
array and some code from gd library. Thanks to Tom Boutell. Thanks to
Kevin J. Walsh. Without Kevin this release would not happen. Thanks to
all of you who showed interest in the counter program. I had fun
writing it.
Authors
Muhammad A Muquit and
Kevin J. Walsh
I like to hear from you
If you are using this program, I like to hear from you. Please add your
web page URL to the database via this form. You can drop me a line if
you like. If you are having any problem with the program, please let me
know as well. Feel free to send any suggestion. If you think that the
program is cool, please consider sending me a picture postcard of the
area where you live. Thanks to all of you who sent me the nice
postcards. I really appreciate it.
I receive enormous number of mails. Please understand that no way I can
answer all of the mails I receive, although eventually I read all the
mails. If you do not hear from me in 3 days, please resend the mail
again.
Muhammad A Muquit
SEMCOR, Inc.
65 West Street Road
Warminster, PA 18974
USA
Thanks.
Enjoy!
ChangeLog
If you contributed or suggested something and if your name is not here,
please drop me a line and get the credit.
Count 2.2 (January 16, 1996)
o There was a logic problem in determining AM and PM. Thanks to
(stephen@txdirect.net). 01/18/96
o Strict mode (detect if browser returns HTTP_REFERER) is a
configurable option.
o An error was in the code related to ACCESS_AUTH directive.
Reported by c2dhanle@CompApp.DCU.IE
Count 2.1 (January 15, 1996)
* The bug related to st parameter is fixed.
* The same program an be used to display time or date.
Count 2.0 (December 27, 1995)
* Configuration scripts. You should not to need to hand edit any
file in order to compile and install the counter.
* Reasonable defaults for all QUERY_STRING parameters.
Implemented by Kevin J. Walsh
* QUERY_STRING parameters can be in any order and not case
sensitive.
Implemented by Kevin J. Walsh
* Counter can be displayed without incrementing.
Implemented by Kevin J. Walsh
* A literal digit string can be displayed.
Implemented by Kevin J. Walsh
* A random digit string can be displayed as counter.
Implemented by Kevin J. Walsh
* Colors can be negated, that is counter can be displayed as a
negative copy.
* The counter can be rotated (integral of 90 degrees, 90,180,270
degrees).
* No need to specify width and height of digit images.
* The frame and transparent color can be a name (e.g. red, violet
etc), a hex string (e.g. ffffff, ff00ff, dddddd etc.) as well as
RGB triplets (e.g. 160;255;0, 0;0;0 etc) as before.
Implemented by Kevin J. Walsh
* The counter can be called as simply as:
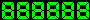 or as complex as before. or any attribute can be set
independently.
Count 2.0b
* in IRIX 5.3 11091810 IP12 mips, if you get an error like
: libCombine.a
: - Too many arguments
*** Error code 1 (bu21)
*** Error code 1 (bu21)
in combine/Makefile, remove the line
$(RANLIB) $@
(Thanks to savarro@CENTRCN.UMontreal.CA).
(12/07/95).
* Log directory was not created by the Count-install script. (Thanks
to robertg@zoom.com). (12/07/95).
Thanks to John Anthony Ruchak for beta testing Count 1.5.
Count 1.5 (September 11, 1995, 9:00 PM EDT)
+ can be compiled with -DALLOW_FILE_CREATION option. if compiled
with this option, the data file will be created if it does not
exist in the directory defined with DataDir and the value defined
with st in QUERY_STRING will be written to it. (suggested by John
Anthony Ruchak.
(September 10, 1995)
+ Advisory data file locking. Datafile will not get messed up by
simultaneous Count.cgi processes.
+ Error messages are converted directly from string to image. No
included GIF images are needed, will be beneficial for system with
low memory. I borrowed the font array and some code from gd
library. Thanks to Tom Boutell
+ Authorized host names can be in configuration file. To handle
"Counter Terrorism", the source code modification is not
necessary.
+ The hits on the web page can be counted without displaying the
digits. suggested by Andres Sepulveda.
Count 1.4 (August 27, 1995)
o wigingto@umr.edu suggested to use HTTP_REFERER for checking remote
access to the counter.
o randerso@bite.db.uth.tmc.edu sent some code segment to account for
port numbers at the end of a referer URL.
o Ornamental frame with user defined color and thickness on the fly.
o maximum number of digits can be >= 5 or <= 10 (if you use md) (on
the fly).
o if pad=0, the exact number of digits will be displayed without
left padding with zeros (on the fly).
o Any color of the digits can be made transparent on the fly.
o Digit style can be provied on the fly.
o sdw@iadfw.net suggested to keep configuration file, data file,
digits, log file in separate directories. It will fix a security
hole.
o datafile can be edited.
Count 1.3
o Hardcoded the base directory of the counter data files. This will
fix a security hole. Thanks to carsten@group.com
----------------------------------------------------------------------------
muquit@semcor.com
Last Update: January 18, 1996
Today: [Image]
[HOME] Home Page
or as complex as before. or any attribute can be set
independently.
Count 2.0b
* in IRIX 5.3 11091810 IP12 mips, if you get an error like
: libCombine.a
: - Too many arguments
*** Error code 1 (bu21)
*** Error code 1 (bu21)
in combine/Makefile, remove the line
$(RANLIB) $@
(Thanks to savarro@CENTRCN.UMontreal.CA).
(12/07/95).
* Log directory was not created by the Count-install script. (Thanks
to robertg@zoom.com). (12/07/95).
Thanks to John Anthony Ruchak for beta testing Count 1.5.
Count 1.5 (September 11, 1995, 9:00 PM EDT)
+ can be compiled with -DALLOW_FILE_CREATION option. if compiled
with this option, the data file will be created if it does not
exist in the directory defined with DataDir and the value defined
with st in QUERY_STRING will be written to it. (suggested by John
Anthony Ruchak.
(September 10, 1995)
+ Advisory data file locking. Datafile will not get messed up by
simultaneous Count.cgi processes.
+ Error messages are converted directly from string to image. No
included GIF images are needed, will be beneficial for system with
low memory. I borrowed the font array and some code from gd
library. Thanks to Tom Boutell
+ Authorized host names can be in configuration file. To handle
"Counter Terrorism", the source code modification is not
necessary.
+ The hits on the web page can be counted without displaying the
digits. suggested by Andres Sepulveda.
Count 1.4 (August 27, 1995)
o wigingto@umr.edu suggested to use HTTP_REFERER for checking remote
access to the counter.
o randerso@bite.db.uth.tmc.edu sent some code segment to account for
port numbers at the end of a referer URL.
o Ornamental frame with user defined color and thickness on the fly.
o maximum number of digits can be >= 5 or <= 10 (if you use md) (on
the fly).
o if pad=0, the exact number of digits will be displayed without
left padding with zeros (on the fly).
o Any color of the digits can be made transparent on the fly.
o Digit style can be provied on the fly.
o sdw@iadfw.net suggested to keep configuration file, data file,
digits, log file in separate directories. It will fix a security
hole.
o datafile can be edited.
Count 1.3
o Hardcoded the base directory of the counter data files. This will
fix a security hole. Thanks to carsten@group.com
----------------------------------------------------------------------------
muquit@semcor.com
Last Update: January 18, 1996
Today: [Image]
[HOME] Home Page